Результат поиска по запросу: "access20management"

Bishkek, Kyrgyzstan - March 14, 2019: Screen of unreal engine game installation software
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую
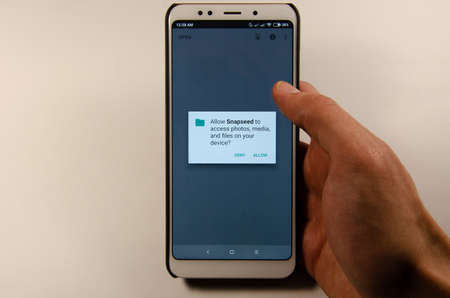
April, 2019. Kramatorsk, Ukraine. Snapseed mobile application on a white smartphone in hand
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Internet, business, Technology and network concept. Cyber security data protection business technology privacy concept.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

3D graphical image of access vertically along with text built by metallic cubic letters from the top perspective, excellent for the concept presentation and slideshows. illustration and background
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

A person's finger is about to touch a glowing shield icon with a gear inside, symbolizing access management. To the right, the words ACCESS MANAGEMENT are displayed next to a digital representation of the world map. The background is a dark blue digital network with interconnected icons.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

CHIANG MAI,THAILAND - May 13, 2022 : Smartphone mobile showing Amazon logo to shopping online. Amazon.com, Inc. American international electronic commerce company.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Text sign showing Account Access. Business showcase having permission to use particular data on a computer Lady In Uniform Holding Tablet In Hand Virtually Typing Futuristic Tech.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

business and security concept. On the red surface there is a lock with a sticker with the inscription - access denied
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Kuala Lumpur, Malaysia, 24th July 2020: Close up Instagram application menu on smartphone screen. Instagram is a photo and video-sharing social networking service owned by Facebook.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

A shadow hacker in front of a computer screen displaying Access Denied in red text, representing cybersecurity threats and hacking.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую
New York, USA - 1 May 2021: SeatGeek company website on screen, Illustrative Editorial
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Device and technology for car parking access control.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Double exposure of man and woman working together and fingerprint hologram drawing. Security concept. Computer background.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Breakout Session write on sticky notes isolated on Wooden Table.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Double exposure of fingerprint hologram and woman holding and using a mobile device. Security concept.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Displaying ACCESS DENIED hologram in server corridor with binary digits and pop-up notifications. Cybersecurity, data center, digital, technology, networking, protection, surveillance
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Tashkent, Uzbekistan - 14 October 2021: Reading breaking news about Popular Netflix new show - Squid games. World press about new South Korean series show - Squid games
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Fingerprint hologram with businessman working on computer on background. Security concept. Double exposure.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

The laptop screen on the table is open. Key word on wooden cubes on laptop. Photographs were taken in the spotlight.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Successful business concept. Businessman working on laptop computer with success button
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

cyber security concept, Login, User, identification information security and encryption, secure access to user's personal information, secure Internet access, cybersecurity.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую
Sign in, get access to a computer system as a guest. Log in message on a digital device screen, closeup view.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Double exposure of fingeprint drawing and cell phone background. Concept of mobile security
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Success button on computer keyboard keys. Business and technology success concept.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Access Word Concept, Blackboard Chalk background Concept Design
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Businessman's Triumph: 'SUCCESS' Held High
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

WROCLAW, POLAND- OCTOBER 05th, 2016: Man launches Tresorit application on Samsung A5.Tresorit is an online cloud storage service with enhanced security and data encryption for Businesses
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

A shadow hacker in front of a computer screen displaying Access Denied in red text, representing cybersecurity threats and hacking.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Access description text words on a keyboard key
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Saving user data. Hacking a password on a PC. Closing access to files. Hackers and secret data. HDD and key with lock..
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

A shadow hacker in front of a computer screen displaying Access Denied in red text, representing cybersecurity threats and hacking.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Fingerprint hologram with businessman working on computer on background. Security concept. Double exposure.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Blue fingerprint hologram over womans hands taking notes background. Concept of protection. Double exposure
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Computer notebook keyboard with Access key
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Double exposure of woman hands working on computer and fingerprint hologram drawing. Top View. Digital Security concept.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

SpaceX company homepage website close-up view. Business and exploration concept background photo
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Accessible Welcome Greeting Welcoming Approachable Access Enter Available Concept
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Blue fingerprint hologram over woman's hands taking notes background. Concept of protection. Double exposure
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Computer notebook keyboard with Access key - technology background
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Double exposure of finger print hologram and cityscape background. Concept of personal security.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую
Estate Planning write on a book isolated wooden table.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

attractive hands writing sign username on a smart phone
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Double exposure of man's hands holding and using a digital device and fingerprint hologram drawing. Security concept.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Double exposure of man's hands typing over computer keyboard and finger print hologram drawing. Top view. Personal security concept.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Not even your smartphone is safe. Shot of an unidentifiable man using a smartphone to hack into a computer network.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Paper note with Username and Password on black computer keyboard. Internet security concept. Close up.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

A shadow hacker in front of a computer screen displaying Access Denied in red text, representing cybersecurity threats and hacking.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Computer on desktop in office with finger print drawing. Double exposure. Concept of business data security.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Use a Document Management System (DMS), an online documentation database, to correctly manage files, knowledge, and documentation in an ERP-enabled company. Corporations' use of technology
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую
CHIANG MAI,THAILAND - APR 11 , 2020 : A working from home employee is downloading the Microsoft Teams social platform, ready for remote working in isolation from home
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

A shadow hacker in front of a computer screen displaying Access Denied in red text, representing cybersecurity threats and hacking.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Smart factory and industry 4.0 and connected production robots exchanging data with internet of things (IoT) with cloud computing technology.Coworking process, entrepreneur team working in creative office space.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

The ACCESS concept word. Business Technology Security Concept
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Close up of businessman using smartwatch and laptop computer in modern office
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Co worker Designer hand using mobile payments online shopping,omni channel,in modern office wooden desk,icons graphic interface screen,eyeglass,filter
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Double exposure of fingerprint hologram and man and woman working together holding and using a mobile device. Security concept
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую
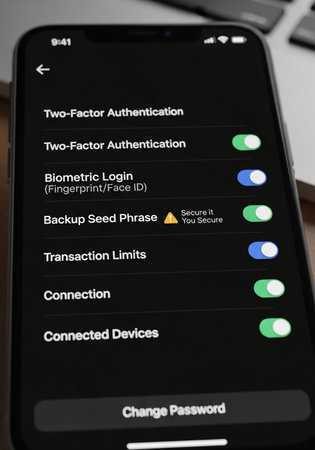
Smartphone displaying security settings including Two-Factor Authentication, Biometric Login, Backup Seed Phrase alert, Transaction Limits, Connection, Connected Devices, and Change Password option.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Document Management System (DMS) Online Document Database and automated processes to manage files, knowledge, and documents in an organization effectively with ERP, enterprise business technology.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Login or Register Login to the system with the online digital world, metaverse security protection system.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Machine learning technology diagram with artificial intelligence (AI),neural network,automation,data mining in VR screen.Team brainstorming task. Photo young creative managers crew working with new startup project.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую
CHIANG MAI, THAILAND - AUG 26, 2020: A woman holds Apple iPhone X with Instagram application on the screen at cafe. Instagram is a photo-sharing app for smartphones.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Bucharest, Romania - April 30, 2020: Shallow depth of field (selective focus) and macro image with the Google Meet mobile application.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Fingerprint hologram with businessman working on computer on background. Security concept. Double exposure.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Double exposure of man's hands holding and using a digital device and fingerprint hologram drawing. Security concept.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Internet, business, Technology and network concept. Cyber security data protection business technology privacy concept.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

The ACCESS concept word. Business Technology Security Concept.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Blue fingerprint hologram over hands taking notes background. Concept of security. Double exposure
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Computer on desktop in office with finger print drawing. Double exposure. Concept of business data security.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

A person activates a digital interface by touching a holographic lock symbol, indicating successful access to a secure system. The environment is dark with glowing screens.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Financial technology flowchart and basic income mining cryptocurrency with blockchain startup unicorn crypto money virtual diagram.Coworking process, entrepreneur team working in creative office space.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую
A shadow hacker in front of a computer screen displaying Access Denied in red text, representing cybersecurity threats and hacking.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Computer on desktop in office with finger print drawing. Double exposure. Concept of business data security.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Fingerprint hologram with businessman working on computer on background. Security concept. Double exposure.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

A finger press red Access button on laptop keyboard.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Asian Woman wash her face in the bathroom after shower.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Success is depicted in futuristic digital design with vibrant blue and red elements, symbolizing achievement and innovation..
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

The ACCESS concept word. Business Technology Security Concept.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

a means of approaching or entering a place. an opening, such as a door, passage, or gate, that allows access to a place
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Computer on desktop in office with finger print drawing. Double exposure. Concept of business data security.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Finger print over computer on the desktop background. Top view. Double exposure. Concept of securitization.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую
New york, USA - November 20, 2020: Add new fingerprint for security on screen laptop close up view
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

BELGRADE, SERBIA - MARCH 9, 2020: Mobile phone with social networking service Instagram. Instagram is an American photo and video-sharing social networking service.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Double exposure of fingerprint hologram and handshake of two men. Security concept.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Paris, France - Nov 10. 2017: enter a passcode when face id is not available new Apple iPhone XS Pro with Face ID virtual facial recognition function with anonymous hacker wearing a mask
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Privacy Access Identification Password Passcode and Privacy
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

The ACCESS concept word. Business Technology Security Concept.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

User showing laptop with remote access on screen and glowing light trails and security icons keywords:...
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Working Together Concept. Small Startup Business Teamwork , User Interface Designer Working on Laptop in Office. Delivery Application Project show on Screen
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Microsoft To Do logo mobile app on the screen smartphone with notebook closeup. Microsoft To Do is a task management app. Moscow, Russia - July 28, 2020
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

A shadow hacker in front of a computer screen displaying Access Denied in red text, representing cybersecurity threats and hacking.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Hand touch virtual global with cyber security concept, Login, User, identification information security and encryption, secure access to user's personal information, secure Internet access, cybersecur
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Laptop with green numbers on display. Smartphone displaying successful login with credentials user and password in the system. Technology communication, security privacy, hacker, cyber crime concept
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

A shadow hacker in front of a computer screen displaying Access Denied in red text, representing cybersecurity threats and hacking.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Hand typing on laptop keyboard to download and upload information data pass thru cloud computing.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Hand holds glowing digital interface with paste icon and image inserted notification Clear detail...
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Grids And Different Set Up Of The Icons Latest Digital Technology Concept
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Key to success. Keys to Success in Business. A conceptual background image. Still Life
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

A shadow hacker in front of a computer screen displaying Access Denied in red text, representing cybersecurity threats and hacking.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Finger print over computer on the desktop background. Top view. Double exposure. Concept of securitization.
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую

Businesswoman pointing his finger touch virtual icon. Modern digital world concept
favorite
Коллекция по умолчанию
Коллекция по умолчанию
Создать новую
Поддержка
Copyright © Legion-Media.





